Bonjour,
Depuis la dernière mise à jour (Core en 4.3.22 et plugin en 2024-01-04), ce dernier n’est pas stable et plante au bout de quelques minutes.
La réinstallation des dépendances ne permet pas de résoudre le problème.
Le réinstallation du plugin non plus.
Je sèche … vous avez une idée ?
Merci d’avance pour votre aide.
FX
Hello,
Je n’ai pas ce plugin, mais je doute que tu auras une réponse sans :
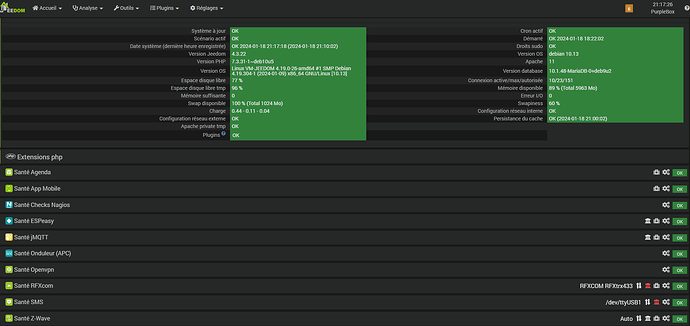
une capture de ta page santé,
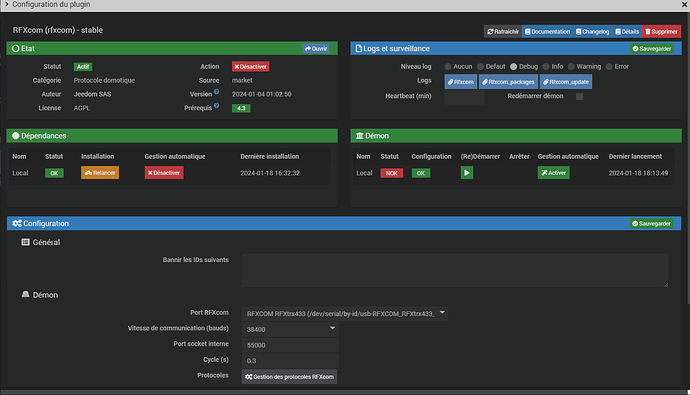
des captures d’écran des configurations,
des logs en debug…
As-tu fait une recherche ou regardé les messages sur le tag plugin-rfxcom ?
Bad
Hello,
J’ai bien fait une recherche avec le tag RFXCOM mais pas trouvé le meme genre de plantage.
Sur la page santé, je ne vois pas grand chose à signaler.
Le démon démarre, des valeurs de sonde remontent puis s’arrête sans message particuliers dans les logs.
La configuration semble bonne bonne dans la mesure où elle marchait et que le démon démarre et remonte des valeurs.
Je pousse des éléments complémentaires ci dessous.
Merci d’avance pour l’aide ![]()
Je ne parviens pas à mettre les logs en raison des limitations appliquées aux nouveaux utilisateurs :
- Pas d’upload de fichier possible
- trop de lien dans les logs (il y a des URL HTTP)
Une idée pour les uploader ?
[EDIT] C’est bon j’ai triché … ca passe dans le message suivant ![]()
C’est illisible un message de 2km.
Il faut faire la même chose mais à l’intérieur d’un Texte préformaté (bouton </>)
Bonsoir,
Voila qui devrait être mieux.
Bonne soirée.
FX
[2024-01-18 21:22:12][INFO] : Lancement démon rfxcomd : /usr/bin/python3 /var/www/html/plugins/rfxcom/resources/rfxcomd/rfxcomd.py --device /dev/serial/by-id/usb-RFXCOM_RFXtrx433_A1HL7VD-if00-port0 --loglevel debug --socketport 55000 --serialrate 38400 --protocol 18 --callback http://127.0.0.1:80/plugins/rfxcom/core/php/jeeRfxcom.php --apikey blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB --cycle 0.3 --pid /tmp/jeedom/rfxcom/deamon.pid
[2024-01-18 21:22:12][INFO] : Start rfxcomd
[2024-01-18 21:22:12][INFO] : Log level : debug
[2024-01-18 21:22:12][INFO] : Socket port : 55000
[2024-01-18 21:22:12][INFO] : Socket host : 127.0.0.1
[2024-01-18 21:22:12][INFO] : PID file : /tmp/jeedom/rfxcom/deamon.pid
[2024-01-18 21:22:12][INFO] : Device : /dev/serial/by-id/usb-RFXCOM_RFXtrx433_A1HL7VD-if00-port0
[2024-01-18 21:22:12][INFO] : Apikey : blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB
[2024-01-18 21:22:12][INFO] : Callback : http://127.0.0.1:80/plugins/rfxcom/core/php/jeeRfxcom.php
[2024-01-18 21:22:12][INFO] : Cycle : 0.3
[2024-01-18 21:22:12][INFO] : Serial rate : 38400
[2024-01-18 21:22:12][INFO] : Serial timeout : 9
[2024-01-18 21:22:12][INFO] : Protocol : 18
[2024-01-18 21:22:12][INFO] : Find device : /dev/serial/by-id/usb-RFXCOM_RFXtrx433_A1HL7VD-if00-port0
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x01 : Interface Response Message
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x02 : Receiver/Transmitter Message
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x10 : Lighting1 (X10, ARC, ELRO, Waveman, EMW200, IMPULS,RisingSun, Philips, Energenie, GDR2, HQ, Oase)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x11 : Lighting2 (AC, HomeEasy EU, ANSLUT, Kambrook)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x13 : Lighting4 (PT2262)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x14 : Lighting5 ( LightwaveRF, Siemens, EMW100, BBSB, MDREMOTE,RSL2, OTIO, Livolo, RGB, Aoke relay, Eurodomest, RGB432W, Legrand,Avantek, IT, Kangtai)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x15 : Lighting6 (Blyss (AE), Cuveo)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x16 : Chime (Byron SX, Byron MP001, SelectPlus, Envivo, Alfawise)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x17 : Fan (Siemens SF01, Itho, LucciAir, SEAV,Westinghouse,Casafan,FT1211R,Novy)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x19 : Blinds1 (RollerTrol,Hasta,A-OK,Raex, Media Mount, DC)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x1C : Edisio
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x1D : Honeywell ActivLink
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x1E : FunkBus
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x1F : Hunter Fan
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x20 : Security1 (X10, KD101, Visonic, Meiantech, SA30, SA33, RM174RF)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x21 : Security2 (KeeLoq)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x28 : Camera1 (Ninja/Robocam)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x30 : Remote control and IR (ATI, Medion, PC Remote)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x40 : Thermostat1 (Digimax)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x42 : Thermostat3 (Mertik-Maxitrol G6R-H4 type)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x4E : BBQ Temperature sensors (BBQ1)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x4F : Temperature and rain sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x50 : Temperature sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x51 : Humidity sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x52 : Temperature and humidity sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x53 : Barometric sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x54 : Temperature, humidity and barometric sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x55 : Rain sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x56 : Wind sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x57 : UV sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x58 : Date/time sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x59 : Current sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x5A : Current sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x5B : Current + ENERGY sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x5C : Power sensors
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x5D : Weighting scale
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x60 : CARTELECTRONIC
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x70 : RFXsensor
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x71 : RFXMeter
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x72 : FS20 (FS20, FHT 8V, FHT80)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x5D : Weighting scale
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x76 : Weather stations (WEATHER1-WEATHER2)
[2024-01-18 21:22:12][DEBUG] : Load decoder packet type 0x77 : SOLAR1
[2024-01-18 21:22:12][DEBUG] : Writing PID 5668 to /tmp/jeedom/rfxcom/deamon.pid
[2024-01-18 21:22:12][DEBUG] : Init request module v2.31.0
[2024-01-18 21:22:12][DEBUG] : Starting new HTTP connection (1): 127.0.0.1:80
[2024-01-18 21:22:12][DEBUG] : null
[2024-01-18 21:22:12][DEBUG] : http://127.0.0.1:80 "GET /plugins/rfxcom/core/php/jeeRfxcom.php?apikey=blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB HTTP/1.1" 200 0
[2024-01-18 21:22:12][DEBUG] : Init serial module v3.5
[2024-01-18 21:22:12][DEBUG] : Start listening...
[2024-01-18 21:22:12][DEBUG] : Socket interface started
[2024-01-18 21:22:12][DEBUG] : LoopNetServer Thread started
[2024-01-18 21:22:12][DEBUG] : Open serial port on device: /dev/serial/by-id/usb-RFXCOM_RFXtrx433_A1HL7VD-if00-port0, rate 38400, timeout : 9
[2024-01-18 21:22:12][DEBUG] : Listening on: [127.0.0.1:55000]
[2024-01-18 21:22:12][DEBUG] : Open Serialport
[2024-01-18 21:22:12][DEBUG] : flushOutput serial port
[2024-01-18 21:22:12][DEBUG] : flushInput serial port
[2024-01-18 21:22:12][DEBUG] : flushOutput serial port
[2024-01-18 21:22:12][DEBUG] : flushInput serial port
[2024-01-18 21:22:12][DEBUG] : Read Socket Thread Launched
[2024-01-18 21:22:12][DEBUG] : Read Device Thread Launched
[2024-01-18 21:22:13][DEBUG] : Send rfxcomd_reset
[2024-01-18 21:22:13][DEBUG] : Write data to serial port : 0d00000000000000000000000000
[2024-01-18 21:22:13][DEBUG] : Sleep 1 sec
[2024-01-18 21:22:14][DEBUG] : flushInput serial port
[2024-01-18 21:22:14][DEBUG] : Send get status test
[2024-01-18 21:22:14][DEBUG] : Write data to serial port : 0d00000102000000000000000000
[2024-01-18 21:22:14][DEBUG] : Message: 1401000102531c0000200001031c0400000000704d
[2024-01-18 21:22:14][DEBUG] : Decode : 1401000102531c0000200001031c0400000000704d
[2024-01-18 21:22:14][DEBUG] : Test message: 1401000102531c0000200001031c0400000000704d
[2024-01-18 21:22:14][DEBUG] : PacketType: 0x01
[2024-01-18 21:22:14][DEBUG] : Length: 21
[2024-01-18 21:22:14][DEBUG] : Start decoding packet type 0x01
[2024-01-18 21:22:14][DEBUG] : Data : {'packetlen': '0x14', 'packettype': '0x01', 'subtype': '0x00', 'seqnbr': '0x01', 'cmnd': '0x02', 'msg1': '0x53', 'msg2': '0x1C', 'msg3': '0x00', 'msg4': '0x00', 'msg5': '0x20', 'msg6': '0x00', 'msg7': '0x01', 'msg8': '0x03', 'msg9': 28, 'msg10': '0x04', 'msg11': '0x00', 'msg12': '0x00', 'msg13': '0x00', 'msg14': '0x00', 'msg15': '0x70', 'msg16': '0x4D'}
[2024-01-18 21:22:14][DEBUG] : Subtype = response on a mode command
[2024-01-18 21:22:14][DEBUG] : Firmware version = 0x1C
[2024-01-18 21:22:14][DEBUG] : RFXtrx433 operating at 433.92MHz
[2024-01-18 21:22:14][DEBUG] : Hardware major version = 0x01
[2024-01-18 21:22:14][DEBUG] : Hardware minor version = 0x03
[2024-01-18 21:22:14][DEBUG] : Output power = 10 dBm
[2024-01-18 21:22:14][DEBUG] : Firmware Ext2
[2024-01-18 21:22:14][DEBUG] : Noise level (only used in special firmware) = 0x00
[2024-01-18 21:22:14][DEBUG] : undec on : 0
[2024-01-18 21:22:14][DEBUG] : Imagintronix,Opus/Alecto2010/Alecto : 0
[2024-01-18 21:22:14][DEBUG] : Byron SX,SelectPlus/Alecto5500 : 0
[2024-01-18 21:22:14][DEBUG] : RSL,Revolt/La Crosse : 0
[2024-01-18 21:22:14][DEBUG] : Lighting4/Davis EU : 0
[2024-01-18 21:22:14][DEBUG] : FineOffset,Viking/Davis US : 0
[2024-01-18 21:22:14][DEBUG] : Rubicson,Alecto,Banggood/Davis AU : 0
[2024-01-18 21:22:14][DEBUG] : AE Blyss : 0
[2024-01-18 21:22:14][DEBUG] : BlindsTx : 0
[2024-01-18 21:22:14][DEBUG] : BlindsT0 : 0
[2024-01-18 21:22:14][DEBUG] : Proguard : 0
[2024-01-18 21:22:14][DEBUG] : Legrand CAD : 0
[2024-01-18 21:22:14][DEBUG] : La Crosse : 0
[2024-01-18 21:22:14][DEBUG] : Hideki,TFA,Cresta,UPM/FS20 : 0
[2024-01-18 21:22:14][DEBUG] : AD LightwaveRF : 0
[2024-01-18 21:22:14][DEBUG] : Mertik/Edisio : 0
[2024-01-18 21:22:14][DEBUG] : Visonic : 0
[2024-01-18 21:22:14][DEBUG] : ATI/cartelectronic/Meiantech,Atlantic : 0
[2024-01-18 21:22:14][DEBUG] : Oregon Scientific/Keeloq : 1
[2024-01-18 21:22:14][DEBUG] : Meiantech,Atlantic/Proguard : 0
[2024-01-18 21:22:14][DEBUG] : HomeEasy EU : 0
[2024-01-18 21:22:14][DEBUG] : AC : 0
[2024-01-18 21:22:14][DEBUG] : ARC : 0
[2024-01-18 21:22:14][DEBUG] : X10 : 0
[2024-01-18 21:22:14][DEBUG] : FunkBus 433.42/Itho CVE RFT : 0
[2024-01-18 21:22:14][DEBUG] : MCZ 434.50/Itho CVE ECO RFT : 0
[2024-01-18 21:22:14][DEBUG] : Honeywell Chime : 0
[2024-01-18 21:22:14][DEBUG] : HomeConfort,Fan : 0
[2024-01-18 21:22:14][DEBUG] : Keeloq : 0
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49056]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"9D01"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49056]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49058]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"4803"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49058]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49066]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"F600"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49066]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49074]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"0C02"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49074]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49076]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"7E02"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49076]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49088]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"C902"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49088]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49090]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"2901"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49090]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49100]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"3F02"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49100]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49104]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"5203"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49104]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49110]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"D003"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49110]
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '9D01'}
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49126]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"6B03"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49126]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49136]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"E701"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49136]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49142]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"3701"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49142]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49158]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"FA02"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49158]
[2024-01-18 21:22:15][DEBUG] : Client connected to [127.0.0.1:49172]
[2024-01-18 21:22:15][DEBUG] : Message read from socket: b'{"apikey":"blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB","cmd":"add","device":{"id":"CB02"}}'
[2024-01-18 21:22:15][DEBUG] : Client disconnected from [127.0.0.1:49172]
[2024-01-18 21:22:15][INFO] : Démon RFXcom lancé
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '4803'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': 'F600'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '0C02'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '7E02'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': 'C902'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '2901'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '3F02'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '5203'}
[2024-01-18 21:22:15][DEBUG] : msg3: [0, 0, 0, 0, 0, 0, 0, 0] / 00
[2024-01-18 21:22:15][DEBUG] : msg4: [0, 0, 0, 0, 0, 0, 0, 0] / 00
[2024-01-18 21:22:15][DEBUG] : msg5: [0, 0, 1, 0, 0, 0, 0, 0] / 20
[2024-01-18 21:22:15][DEBUG] : msg6: [0, 0, 0, 0, 0, 0, 0, 0] / 00
[2024-01-18 21:22:15][DEBUG] : Command: 0d00000203531C00002000000000
[2024-01-18 21:22:15][DEBUG] : Protocol actually activated 00002000
[2024-01-18 21:22:15][DEBUG] : Actual Frequency 53
[2024-01-18 21:22:15][DEBUG] : Wanted protocol 00002000
[2024-01-18 21:22:15][DEBUG] : All is ok, sending start
[2024-01-18 21:22:15][DEBUG] : Write data to serial port : 0d00000207000000000000000000
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': 'D003'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '6B03'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': 'E701'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': '3701'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': 'FA02'}
[2024-01-18 21:22:15][DEBUG] : Message received in socket JEEDOM_SOCKET_MESSAGE
[2024-01-18 21:22:15][DEBUG] : Add device : {'id': 'CB02'}
[2024-01-18 21:22:15][DEBUG] : Message: 1401070207436f7079726967687420524658434f4d
[2024-01-18 21:22:15][DEBUG] : Decode : 1401070207436f7079726967687420524658434f4d
[2024-01-18 21:22:15][DEBUG] : Test message: 1401070207436f7079726967687420524658434f4d
[2024-01-18 21:22:15][DEBUG] : PacketType: 0x01
[2024-01-18 21:22:15][DEBUG] : Length: 21
[2024-01-18 21:22:15][DEBUG] : Start decoding packet type 0x01
[2024-01-18 21:22:15][DEBUG] : Data : {'packetlen': '0x14', 'packettype': '0x01', 'subtype': '0x07', 'seqnbr': '0x02', 'cmnd': '0x07', 'msg1': '0x43', 'msg2': '0x6F', 'msg3': '0x70', 'msg4': '0x79', 'msg5': '0x72', 'msg6': '0x69', 'msg7': '0x67', 'msg8': '0x68', 'msg9': 116, 'msg10': '0x20', 'msg11': '0x52', 'msg12': '0x46', 'msg13': '0x58', 'msg14': '0x43', 'msg15': '0x4F', 'msg16': '0x4D'}
[2024-01-18 21:22:15][DEBUG] : Subtype = start RFXtrx receiver
[2024-01-18 21:22:22][DEBUG] : Message: 135b0100f600010105000000a600000000000070
[2024-01-18 21:22:22][DEBUG] : Decode : 135b0100f600010105000000a600000000000070
[2024-01-18 21:22:22][DEBUG] : Test message: 135b0100f600010105000000a600000000000070
[2024-01-18 21:22:22][DEBUG] : PacketType: 0x5B
[2024-01-18 21:22:22][DEBUG] : Length: 20
[2024-01-18 21:22:22][DEBUG] : Start decoding packet type 0x5B
[2024-01-18 21:22:22][DEBUG] : Subtype = ELEC4 is CM180i
[2024-01-18 21:22:22][DEBUG] : Data : {'packetlen': '0x13', 'packettype': '0x5B', 'subtype': '0x01', 'seqnbr': '0x00', 'id1': '0xF6', 'id2': '0x00', 'count': 1, 'ch1': 261, 'ch2': 0, 'ch3': 166, 'total': 0, 'battery': 10, 'rssi': 7}
[2024-01-18 21:22:22][DEBUG] : Decoded info : {'packettype': '0x5B', 'subtype': '0x01', 'id': 'F600', 'count': 1, 'ch1': 26.1, 'ch2': 0.0, 'ch3': 16.6, 'total': 0.0, 'battery': 10, 'rssi': 7}
[2024-01-18 21:22:22][DEBUG] : Device is known id : F600
[2024-01-18 21:22:22][DEBUG] : Send to jeedom : {'devices': {'F6005B': {'packettype': '0x5B', 'subtype': '0x01', 'id': 'F600', 'count': 1, 'ch1': 26.1, 'ch2': 0.0, 'ch3': 16.6, 'total': 0.0, 'battery': 10, 'rssi': 7}}}
[2024-01-18 21:22:22][DEBUG] : Starting new HTTP connection (1): 127.0.0.1:80
[2024-01-18 21:22:22][DEBUG] : {"devices":{"F6005B":{"packettype":"0x5B","subtype":"0x01","id":"F600","count":1,"ch1":26.1,"ch2":0,"ch3":16.6,"total":0,"battery":10,"rssi":7}}}
[2024-01-18 21:22:22][DEBUG] : http://127.0.0.1:80 "POST /plugins/rfxcom/core/php/jeeRfxcom.php?apikey=blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB HTTP/1.1" 200 0
[2024-01-18 21:22:34][DEBUG] : Message: 135b0101f600000147000000a50001af73e47270
[2024-01-18 21:22:34][DEBUG] : Decode : 135b0101f600000147000000a50001af73e47270
[2024-01-18 21:22:34][DEBUG] : Test message: 135b0101f600000147000000a50001af73e47270
[2024-01-18 21:22:34][DEBUG] : PacketType: 0x5B
[2024-01-18 21:22:34][DEBUG] : Length: 20
[2024-01-18 21:22:34][DEBUG] : Start decoding packet type 0x5B
[2024-01-18 21:22:34][DEBUG] : Subtype = ELEC4 is CM180i
[2024-01-18 21:22:34][DEBUG] : Data : {'packetlen': '0x13', 'packettype': '0x5B', 'subtype': '0x01', 'seqnbr': '0x01', 'id1': '0xF6', 'id2': '0x00', 'count': 0, 'ch1': 327, 'ch2': 0, 'ch3': 165, 'total': 7238575218, 'battery': 10, 'rssi': 7}
[2024-01-18 21:22:34][DEBUG] : Decoded info : {'packettype': '0x5B', 'subtype': '0x01', 'id': 'F600', 'count': 0, 'ch1': 32.7, 'ch2': 0.0, 'ch3': 16.5, 'total': 32363323.97, 'battery': 10, 'rssi': 7}
[2024-01-18 21:22:34][DEBUG] : Device is known id : F600
[2024-01-18 21:22:34][DEBUG] : Send to jeedom : {'devices': {'F6005B': {'packettype': '0x5B', 'subtype': '0x01', 'id': 'F600', 'count': 0, 'ch1': 32.7, 'ch2': 0.0, 'ch3': 16.5, 'total': 32363323.97, 'battery': 10, 'rssi': 7}}}
[2024-01-18 21:22:34][DEBUG] : Starting new HTTP connection (1): 127.0.0.1:80
[2024-01-18 21:22:34][DEBUG] : {"devices":{"F6005B":{"packettype":"0x5B","subtype":"0x01","id":"F600","count":0,"ch1":32.7,"ch2":0,"ch3":16.5,"total":32363323.97,"battery":10,"rssi":7}}}
[2024-01-18 21:22:34][DEBUG] : http://127.0.0.1:80 "POST /plugins/rfxcom/core/php/jeeRfxcom.php?apikey=blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB HTTP/1.1" 200 0
[2024-01-18 21:22:46][DEBUG] : Message: 135b0102f600040126000000a500000000000070
[2024-01-18 21:22:46][DEBUG] : Decode : 135b0102f600040126000000a500000000000070
[2024-01-18 21:22:46][DEBUG] : Test message: 135b0102f600040126000000a500000000000070
[2024-01-18 21:22:46][DEBUG] : PacketType: 0x5B
[2024-01-18 21:22:46][DEBUG] : Length: 20
....[log tronqué car trop long]
[2024-01-18 21:24:58][DEBUG] : Start decoding packet type 0x5B
[2024-01-18 21:24:58][DEBUG] : Subtype = ELEC4 is CM180i
[2024-01-18 21:24:58][DEBUG] : Data : {'packetlen': '0x13', 'packettype': '0x5B', 'subtype': '0x01', 'seqnbr': '0x0B', 'id1': '0xF6', 'id2': '0x00', 'count': 3, 'ch1': 207, 'ch2': 0, 'ch3': 166, 'total': 0, 'battery': 10, 'rssi': 7}
[2024-01-18 21:24:58][DEBUG] : Decoded info : {'packettype': '0x5B', 'subtype': '0x01', 'id': 'F600', 'count': 3, 'ch1': 20.7, 'ch2': 0.0, 'ch3': 16.6, 'total': 0.0, 'battery': 10, 'rssi': 7}
[2024-01-18 21:24:58][DEBUG] : Device is known id : F600
[2024-01-18 21:24:58][DEBUG] : Send to jeedom : {'devices': {'F6005B': {'packettype': '0x5B', 'subtype': '0x01', 'id': 'F600', 'count': 3, 'ch1': 20.7, 'ch2': 0.0, 'ch3': 16.6, 'total': 0.0, 'battery': 10, 'rssi': 7}}}
[2024-01-18 21:24:58][DEBUG] : Starting new HTTP connection (1): 127.0.0.1:80
[2024-01-18 21:24:58][DEBUG] : {"devices":{"F6005B":{"packettype":"0x5B","subtype":"0x01","id":"F600","count":3,"ch1":20.7,"ch2":0,"ch3":16.6,"total":0,"battery":10,"rssi":7}}}
[2024-01-18 21:24:58][DEBUG] : http://127.0.0.1:80 "POST /plugins/rfxcom/core/php/jeeRfxcom.php?apikey=blreBppv8pU047WgbTbgpeSwVM2b9YUXHFq4yTVyHESIZxpB HTTP/1.1" 200 0
Y a aucune erreur, il n’a pas l’air de planter là.
Il faudrait voir le log avec l’erreur ensuite vous pourrez chercher cette erreur sur community, la solution s’y trouve peut-être.
Si trop de log et que vous perdez l’erreur, repassez le log en info et relancer le démon
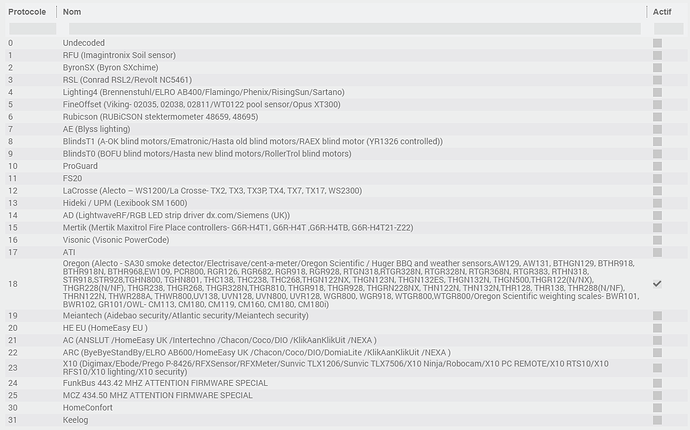
Faudrait voir quel firmware est mis ds le rfx
Ensuite quels protocols sont activés
J’ai l’impression qu’ils sont tous activés non?
Ils se chargent avec load decoder packet type?
Tu peux essayer de désactiver tous les protocoles et de les remettre un à un. Si tu les as tous activés, certains ne sont pas compatibles entre eux.
C’est pour cela que je souligne la chose.
Dans la doc de rfx lui meme il est bien dit que certains protocoles sont incompatibles entre eux.
Idem fonction du firmware …
Hello,
J’ai tenté avec le log en mode « info » mais j’ai rien.
Il ne crache pas de log avant de planter.
Je confirme que le démon fonctionne mais au bout d’un moment, c’est plantage sans crier gare.
J’ai commencé à regarder au niveau des logs de l’OS mais j’ai rien trouvé pour le moment.
Avez-vous une piste de ce côté ?
A+
FX
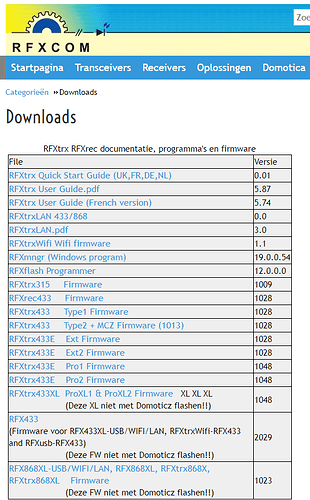
Le firmware a été mis à jour mais ca changé le fonctionnement du démon.
J’ai supprimé également tous les protocoles inutiles, je suis en config mini :
Comme déjà dit et resté sans réponse
J’ai dit cela car j’ai eu le coup !
Depuis la MAJ du firmware en RFXtrx433_Ext_1028, plus de souci !
Idem j’ai fait gaffe de pas activer les protocoles que je n’utilise pas
Les numéros de firmware sont codés dans les logs … c’est le bordel ![]()
En tout cas hier j’ai passé celui là : RFXtrx433_Ext2_1028.hex
Il faut peut-être que je tente le Ext1 …
Je pense que tu devrais tester le même que moi
C’est pas mieux …
De mémoire, il me semble que mon paternel avait eu un souci comme ça à s’arracher les cheveux !
C’était le cable usb entre le rfx et la box. Celui d’origine était pas top.
Après changement il avait plus jamais eu de souci.
A voir si tu peux tester cela.
Même souci pour un rflink. Le fournisseur devait être le même ![]()
Antoine
Hello,
Même après le changement du cable, le démon plante.
J’ai tenté de changer de port USB sur le PC, idem
J’ai tenté de changer la vitesse, marche pas non plus …
Je désespère ![]()
Des idées pour analyser le plantage directement dans l’OS Debian ?
Bonne journée.
FX