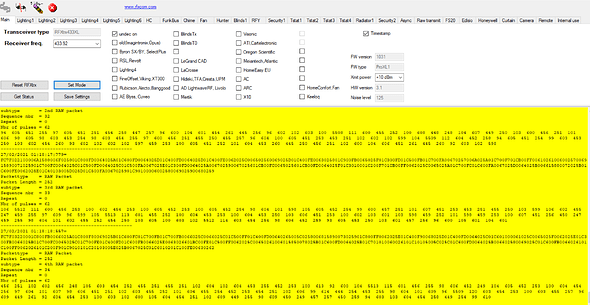
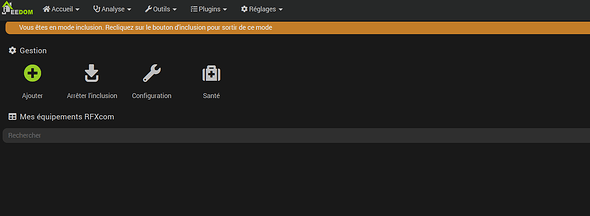
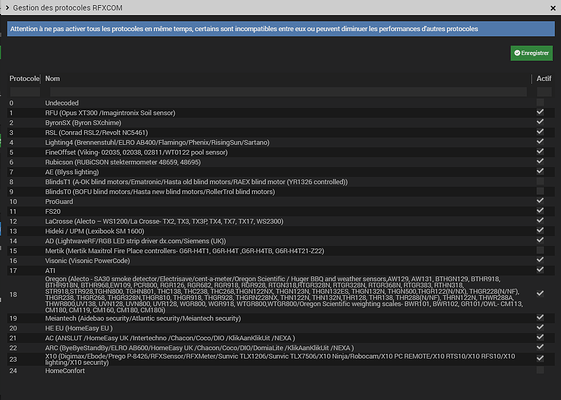
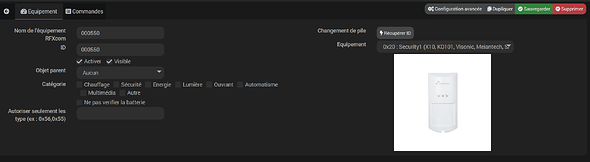
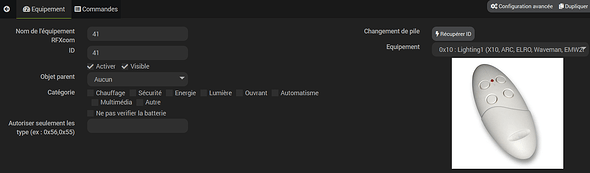
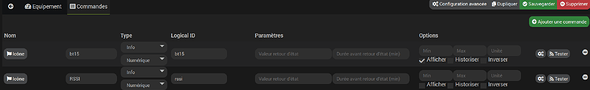
Voici avec plusieurs tlcmd en appuyant sur on/off
[2021-02-27 17:37:19][DEBUG] : Signal 15 caught, exiting...
[2021-02-27 17:37:19][DEBUG] : Shutdown
[2021-02-27 17:37:19][DEBUG] : Removing PID file /tmp/jeedom/rfxcom/deamon.pid
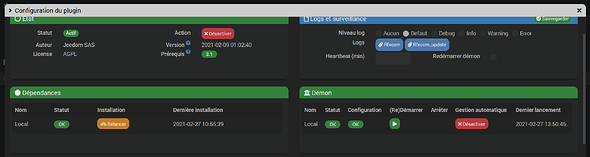
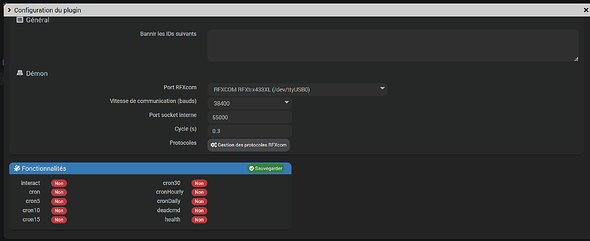
[2021-02-27 18:37:22][INFO] : Lancement démon rfxcomd : /usr/bin/python3 /var/www/html/plugins/rfxcom/resources/rfxcomd/rfxcomd.py --device /dev/ttyUSB0 --loglevel debug --socketport 55000 --serialrate 38400 --protocol 1,2,3,4,5,6,7,10,11,12,13,14,16,17,19,20,21,22,23 --callback http://127.0.0.1:80/plugins/rfxcom/core/php/jeeRfxcom.php --apikey H6qGHrufDTZdSfwMh6fvb2JE5R084ms4 --cycle 0.3 --pid /tmp/jeedom/rfxcom/deamon.pid
[2021-02-27 17:37:23][INFO] : Start rfxcomd
[2021-02-27 17:37:23][INFO] : Log level : debug
[2021-02-27 17:37:23][INFO] : Socket port : 55000
[2021-02-27 17:37:23][INFO] : Socket host : 127.0.0.1
[2021-02-27 17:37:23][INFO] : PID file : /tmp/jeedom/rfxcom/deamon.pid
[2021-02-27 17:37:23][INFO] : Device : /dev/ttyUSB0
[2021-02-27 17:37:23][INFO] : Apikey : H6qGHrufDTZdSfwMh6fvb2JE5R084ms4
[2021-02-27 17:37:23][INFO] : Callback : http://127.0.0.1:80/plugins/rfxcom/core/php/jeeRfxcom.php
[2021-02-27 17:37:23][INFO] : Cycle : 0.3
[2021-02-27 17:37:23][INFO] : Serial rate : 38400
[2021-02-27 17:37:23][INFO] : Serial timeout : 9
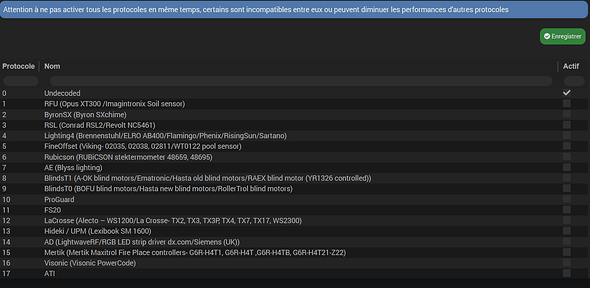
[2021-02-27 17:37:23][INFO] : Protocol : 1,2,3,4,5,6,7,10,11,12,13,14,16,17,19,20,21,22,23
[2021-02-27 17:37:23][INFO] : Find device : /dev/ttyUSB0
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x01 : Interface Response Message
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x02 : Receiver/Transmitter Message
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x10 : Lighting1 (X10, ARC, ELRO, Waveman, EMW200, IMPULS,RisingSun, Philips, Energenie, GDR2, HQ, Oase)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x11 : Lighting2 (AC, HomeEasy EU, ANSLUT, Kambrook)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x13 : Lighting4 (PT2262)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x14 : Lighting5 ( LightwaveRF, Siemens, EMW100, BBSB, MDREMOTE,RSL2, OTIO, Livolo, RGB, Aoke relay, Eurodomest, RGB432W, Legrand,Avantek, IT, Kangtai)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x15 : Lighting6 (Blyss (AE), Cuveo)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x16 : Chime (Byron SX, Byron MP001, SelectPlus, Envivo, Alfawise)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x17 : Fan (Siemens SF01, Itho, LucciAir, SEAV,Westinghouse,Casafan,FT1211R,Novy)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x19 : Blinds1 (RollerTrol,Hasta,A-OK,Raex, Media Mount, DC)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x1C : Edisio
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x1D : Honeywell ActivLink
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x1E : FunkBus
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x1F : Hunter Fan
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x20 : Security1 (X10, KD101, Visonic, Meiantech, SA30, SA33, RM174RF)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x21 : Security2 (KeeLoq)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x28 : Camera1 (Ninja/Robocam)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x30 : Remote control and IR (ATI, Medion, PC Remote)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x40 : Thermostat1 (Digimax)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x42 : Thermostat3 (Mertik-Maxitrol G6R-H4 type)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x4E : BBQ Temperature sensors (BBQ1)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x4F : Temperature and rain sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x50 : Temperature sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x51 : Humidity sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x52 : Temperature and humidity sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x53 : Barometric sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x54 : Temperature, humidity and barometric sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x55 : Rain sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x56 : Wind sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x57 : UV sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x58 : Date/time sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x59 : Current sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x5A : Current sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x5B : Current + ENERGY sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x5C : Power sensors
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x5D : Weighting scale
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x60 : CARTELECTRONIC
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x70 : RFXsensor
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x71 : RFXMeter
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x72 : FS20 (FS20, FHT 8V, FHT80)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x76 : Weather stations (WEATHER1-WEATHER2)
[2021-02-27 17:37:23][DEBUG] : Load decoder packet type 0x77 : SOLAR1
[2021-02-27 17:37:23][DEBUG] : Writing PID 30082 to /tmp/jeedom/rfxcom/deamon.pid
[2021-02-27 17:37:23][DEBUG] : Init request module v2.21.0
[2021-02-27 17:37:23][DEBUG] : Starting new HTTP connection (1): 127.0.0.1:80
[2021-02-27 18:37:23][DEBUG] : null
[2021-02-27 17:37:23][DEBUG] : http://127.0.0.1:80 "GET /plugins/rfxcom/core/php/jeeRfxcom.php?apikey=H6qGHrufDTZdSfwMh6fvb2JE5R084ms4 HTTP/1.1" 200 0
[2021-02-27 17:37:23][DEBUG] : Init serial module v3.5
[2021-02-27 17:37:23][DEBUG] : Start listening...
[2021-02-27 17:37:23][DEBUG] : Socket interface started
[2021-02-27 17:37:23][DEBUG] : LoopNetServer Thread started
[2021-02-27 17:37:23][DEBUG] : Open serial port on device: /dev/ttyUSB0, rate 38400, timeout : 9
[2021-02-27 17:37:23][DEBUG] : Listening on: [127.0.0.1:55000]
[2021-02-27 17:37:23][DEBUG] : Open Serialport
[2021-02-27 17:37:23][DEBUG] : flushOutput serial port
[2021-02-27 17:37:23][DEBUG] : flushInput serial port
[2021-02-27 17:37:23][DEBUG] : flushOutput serial port
[2021-02-27 17:37:23][DEBUG] : flushInput serial port
[2021-02-27 17:37:23][DEBUG] : Read Socket Thread Launched
[2021-02-27 17:37:23][DEBUG] : Read Device Thread Launched
[2021-02-27 17:37:24][DEBUG] : Send rfxcomd_reset
[2021-02-27 17:37:24][DEBUG] : Write data to serial port : 0d00000000000000000000000000
[2021-02-27 17:37:24][DEBUG] : Sleep 1 sec
[2021-02-27 17:37:25][DEBUG] : flushInput serial port
[2021-02-27 17:37:25][DEBUG] : Send get status test
[2021-02-27 17:37:25][DEBUG] : Write data to serial port : 0d00000102000000000000000000
[2021-02-27 17:37:25][DEBUG] : Message: 1401000102532b7f3edf0003011c107a4658434f4d
[2021-02-27 17:37:25][DEBUG] : Decode : 1401000102532b7f3edf0003011c107a4658434f4d
[2021-02-27 17:37:25][DEBUG] : Test message: 1401000102532b7f3edf0003011c107a4658434f4d
[2021-02-27 17:37:25][DEBUG] : PacketType: 0x01
[2021-02-27 17:37:25][DEBUG] : Length: 21
[2021-02-27 17:37:25][DEBUG] : Start decoding packet type 0x01
[2021-02-27 17:37:25][DEBUG] : Data : {'packetlen': '0x14', 'packettype': '0x01', 'subtype': '0x00', 'seqnbr': '0x01', 'cmnd': '0x02', 'msg1': '0x53', 'msg2': '0x2B', 'msg3': '0x7F', 'msg4': '0x3E', 'msg5': '0xDF', 'msg6': '0x00', 'msg7': '0x03', 'msg8': '0x01', 'msg9': 28, 'msg10': '0x10', 'msg11': '0x7A', 'msg12': '0x46', 'msg13': '0x58', 'msg14': '0x43', 'msg15': '0x4F', 'msg16': '0x4D'}
[2021-02-27 17:37:25][DEBUG] : Subtype = response on a mode command
[2021-02-27 17:37:25][DEBUG] : Firmware version = 0x2B
[2021-02-27 17:37:25][DEBUG] : RFXtrx433 operating at 433.92MHz
[2021-02-27 17:37:25][DEBUG] : Hardware major version = 0x03
[2021-02-27 17:37:25][DEBUG] : Hardware minor version = 0x01
[2021-02-27 17:37:25][DEBUG] : Output power = 10 dBm
[2021-02-27 17:37:25][DEBUG] : Firmware ProXL1
[2021-02-27 17:37:25][DEBUG] : Noise level (only used in special firmware) = 0x7A
[2021-02-27 17:37:25][DEBUG] : undec on : 0
[2021-02-27 17:37:25][DEBUG] : Imagintronix,Opus/Alecto2010/Alecto : 1
[2021-02-27 17:37:25][DEBUG] : Byron SX,SelectPlus/Alecto5500 : 1
[2021-02-27 17:37:25][DEBUG] : RSL,Revolt/La Crosse : 1
[2021-02-27 17:37:25][DEBUG] : Lighting4/Davis EU : 1
[2021-02-27 17:37:25][DEBUG] : FineOffset,Viking/Davis US : 1
[2021-02-27 17:37:25][DEBUG] : Rubicson,Alecto,Banggood/Davis AU : 1
[2021-02-27 17:37:25][DEBUG] : AE Blyss : 1
[2021-02-27 17:37:25][DEBUG] : BlindsTx : 0
[2021-02-27 17:37:25][DEBUG] : BlindsT0 : 0
[2021-02-27 17:37:25][DEBUG] : Proguard : 1
[2021-02-27 17:37:25][DEBUG] : Legrand CAD : 1
[2021-02-27 17:37:25][DEBUG] : La Crosse : 1
[2021-02-27 17:37:25][DEBUG] : Hideki,TFA,Cresta,UPM/FS20 : 1
[2021-02-27 17:37:25][DEBUG] : AD LightwaveRF : 1
[2021-02-27 17:37:25][DEBUG] : Mertik/Edisio : 0
[2021-02-27 17:37:25][DEBUG] : Visonic : 1
[2021-02-27 17:37:25][DEBUG] : ATI/cartelectronic/Meiantech,Atlantic : 1
[2021-02-27 17:37:25][DEBUG] : Oregon Scientific/Keeloq : 0
[2021-02-27 17:37:25][DEBUG] : Meiantech,Atlantic/Proguard : 1
[2021-02-27 17:37:25][DEBUG] : HomeEasy EU : 1
[2021-02-27 17:37:25][DEBUG] : AC : 1
[2021-02-27 17:37:25][DEBUG] : ARC : 1
[2021-02-27 17:37:25][DEBUG] : X10 : 1
[2021-02-27 17:37:25][DEBUG] : FunkBus 433.42/Itho CVE RFT : 0
[2021-02-27 17:37:25][DEBUG] : MCZ 434.50/Itho CVE ECO RFT : 0
[2021-02-27 17:37:25][DEBUG] : Honeywell Chime : 0
[2021-02-27 17:37:25][DEBUG] : HomeConfort,Fan : 0
[2021-02-27 17:37:25][DEBUG] : Keeloq : 0
[2021-02-27 18:37:25][INFO] : Démon RFXcom lancé
[2021-02-27 17:37:26][DEBUG] : msg3: [0, 1, 1, 1, 1, 1, 1, 1] / 7f
[2021-02-27 17:37:26][DEBUG] : msg4: [0, 0, 1, 1, 1, 1, 1, 0] / 3e
[2021-02-27 17:37:26][DEBUG] : msg5: [1, 1, 0, 1, 1, 1, 1, 1] / df
[2021-02-27 17:37:26][DEBUG] : msg6: [0, 0, 0, 0, 0, 0, 0, 0] / 00
[2021-02-27 17:37:26][DEBUG] : Command: 0d00000203531C7f3edf00000000
[2021-02-27 17:37:26][DEBUG] : Protocol actually activated 7f3edf00
[2021-02-27 17:37:26][DEBUG] : Actual Frequency 53
[2021-02-27 17:37:26][DEBUG] : Wanted protocol 7f3edf00
[2021-02-27 17:37:37][DEBUG] : Message: 082000005415500289
[2021-02-27 17:37:37][DEBUG] : Decode : 082000005415500289
[2021-02-27 17:37:37][DEBUG] : Test message: 082000005415500289
[2021-02-27 17:37:37][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:37][DEBUG] : Length: 9
[2021-02-27 17:37:37][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:37][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:37][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x00', 'id1': '0x54', 'id2': '0x15', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:37][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '541550', 'status': 2, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:37][DEBUG] : unknown device id : 541550
[2021-02-27 17:37:38][DEBUG] : Message: 082000015415500b79
[2021-02-27 17:37:38][DEBUG] : Decode : 082000015415500b79
[2021-02-27 17:37:38][DEBUG] : Test message: 082000015415500b79
[2021-02-27 17:37:38][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:38][DEBUG] : Length: 9
[2021-02-27 17:37:38][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:38][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:38][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x01', 'id1': '0x54', 'id2': '0x15', 'id3': '0x50', 'status': 11, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:38][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '541550', 'status': 11, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:38][DEBUG] : unknown device id : 541550
[2021-02-27 17:37:39][DEBUG] : Message: 082000025455500279
[2021-02-27 17:37:39][DEBUG] : Decode : 082000025455500279
[2021-02-27 17:37:39][DEBUG] : Test message: 082000025455500279
[2021-02-27 17:37:39][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:39][DEBUG] : Length: 9
[2021-02-27 17:37:39][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:39][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:39][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x02', 'id1': '0x54', 'id2': '0x55', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:39][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '545550', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:39][DEBUG] : unknown device id : 545550
[2021-02-27 17:37:39][DEBUG] : Message: 082000035445500279
[2021-02-27 17:37:39][DEBUG] : Decode : 082000035445500279
[2021-02-27 17:37:39][DEBUG] : Test message: 082000035445500279
[2021-02-27 17:37:39][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:39][DEBUG] : Length: 9
[2021-02-27 17:37:39][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:39][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:39][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x03', 'id1': '0x54', 'id2': '0x45', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:39][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '544550', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:39][DEBUG] : unknown device id : 544550
[2021-02-27 17:37:39][DEBUG] : Message: 082000045455500279
[2021-02-27 17:37:39][DEBUG] : Decode : 082000045455500279
[2021-02-27 17:37:39][DEBUG] : Test message: 082000045455500279
[2021-02-27 17:37:39][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:39][DEBUG] : Length: 9
[2021-02-27 17:37:39][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:39][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:39][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x04', 'id1': '0x54', 'id2': '0x55', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:39][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '545550', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:39][DEBUG] : unknown device id : 545550
[2021-02-27 17:37:40][DEBUG] : Message: 082000055445500b89
[2021-02-27 17:37:40][DEBUG] : Decode : 082000055445500b89
[2021-02-27 17:37:40][DEBUG] : Test message: 082000055445500b89
[2021-02-27 17:37:40][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:40][DEBUG] : Length: 9
[2021-02-27 17:37:40][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:40][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:40][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x05', 'id1': '0x54', 'id2': '0x45', 'id3': '0x50', 'status': 11, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:40][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '544550', 'status': 11, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:40][DEBUG] : unknown device id : 544550
[2021-02-27 17:37:40][DEBUG] : Message: 082000065455500279
[2021-02-27 17:37:40][DEBUG] : Decode : 082000065455500279
[2021-02-27 17:37:40][DEBUG] : Test message: 082000065455500279
[2021-02-27 17:37:40][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:40][DEBUG] : Length: 9
[2021-02-27 17:37:40][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:40][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:40][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x06', 'id1': '0x54', 'id2': '0x55', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:40][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '545550', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:40][DEBUG] : unknown device id : 545550
[2021-02-27 17:37:42][DEBUG] : Message: 082000075451500289
[2021-02-27 17:37:42][DEBUG] : Decode : 082000075451500289
[2021-02-27 17:37:42][DEBUG] : Test message: 082000075451500289
[2021-02-27 17:37:42][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:42][DEBUG] : Length: 9
[2021-02-27 17:37:42][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:42][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:42][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x07', 'id1': '0x54', 'id2': '0x51', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:42][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '545150', 'status': 2, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:42][DEBUG] : unknown device id : 545150
[2021-02-27 17:37:42][DEBUG] : Message: 082000085455500279
[2021-02-27 17:37:42][DEBUG] : Decode : 082000085455500279
[2021-02-27 17:37:42][DEBUG] : Test message: 082000085455500279
[2021-02-27 17:37:42][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:42][DEBUG] : Length: 9
[2021-02-27 17:37:42][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:42][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:42][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x08', 'id1': '0x54', 'id2': '0x55', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:42][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '545550', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:42][DEBUG] : unknown device id : 545550
[2021-02-27 17:37:43][DEBUG] : Message: 082000095451500b89
[2021-02-27 17:37:43][DEBUG] : Decode : 082000095451500b89
[2021-02-27 17:37:43][DEBUG] : Test message: 082000095451500b89
[2021-02-27 17:37:43][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:43][DEBUG] : Length: 9
[2021-02-27 17:37:43][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:43][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:43][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x09', 'id1': '0x54', 'id2': '0x51', 'id3': '0x50', 'status': 11, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:43][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '545150', 'status': 11, 'battery': 9, 'rssi': 8}
[2021-02-27 17:37:43][DEBUG] : unknown device id : 545150
[2021-02-27 17:37:43][DEBUG] : Message: 0820000a5455500279
[2021-02-27 17:37:43][DEBUG] : Decode : 0820000a5455500279
[2021-02-27 17:37:43][DEBUG] : Test message: 0820000a5455500279
[2021-02-27 17:37:43][DEBUG] : PacketType: 0x20
[2021-02-27 17:37:43][DEBUG] : Length: 9
[2021-02-27 17:37:43][DEBUG] : Start decoding packet type 0x20
[2021-02-27 17:37:43][DEBUG] : Subtype = X10 security door/window sensor
[2021-02-27 17:37:43][DEBUG] : Data : {'packetlen': '0x08', 'packettype': '0x20', 'subtype': '0x00', 'seqnbr': '0x0A', 'id1': '0x54', 'id2': '0x55', 'id3': '0x50', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:43][DEBUG] : Decoded info : {'packettype': '0x20', 'subtype': '0x00', 'id': '545550', 'status': 2, 'battery': 9, 'rssi': 7}
[2021-02-27 17:37:43][DEBUG] : unknown device id : 545550