Voici le log DNS complet :
0000|2024-07-26 01:05:44 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
0001|2024-07-26 01:05:44 --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
0002|2024-07-26 01:05:44 WARNING: file '/tmp/jeedom/openvpn/openvpn_auth_BsVWAFFKsZex8vkugda9Jss2C8NN9l.conf' is group or others accessible
0003|2024-07-26 01:05:44 OpenVPN 2.5.1 aarch64-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on May 14 2021
0004|2024-07-26 01:05:44 library versions: OpenSSL 1.1.1w 11 Sep 2023, LZO 2.10
0005|2024-07-26 01:05:44 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
0006|2024-07-26 01:05:44 TCP/UDP: Preserving recently used remote address: [AF_INET]51.159.170.131:1201
0007|2024-07-26 01:05:44 UDP link local: (not bound)
0008|2024-07-26 01:05:44 UDP link remote: [AF_INET]51.159.170.131:1201
0009|2024-07-26 01:05:44 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0010|2024-07-26 01:05:44 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
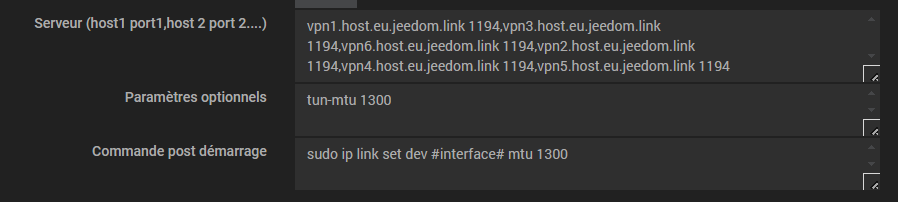
0011|2024-07-26 01:05:45 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0012|2024-07-26 01:05:45 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0013|2024-07-26 01:05:45 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0014|2024-07-26 01:05:45 [server] Peer Connection Initiated with [AF_INET]51.159.170.131:1201
0015|2024-07-26 01:05:45 Data Channel: using negotiated cipher 'AES-256-GCM'
0016|2024-07-26 01:05:45 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0017|2024-07-26 01:05:45 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0018|2024-07-26 01:05:45 TUN/TAP device tun1 opened
0019|2024-07-26 01:05:45 net_iface_mtu_set: mtu 1500 for tun1
0020|2024-07-26 01:05:45 net_iface_up: set tun1 up
0021|2024-07-26 01:05:45 net_addr_ptp_v4_add: 10.16.34.202 peer 10.16.34.201 dev tun1
0022|2024-07-26 01:05:45 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
0023|2024-07-26 01:05:45 Initialization Sequence Completed
0024|2024-07-26 02:05:04 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0025|2024-07-26 02:05:04 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0026|2024-07-26 02:05:04 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0027|2024-07-26 02:05:04 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0028|2024-07-26 02:05:04 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0029|2024-07-26 02:05:04 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0030|2024-07-26 02:05:04 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0031|2024-07-26 03:04:23 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0032|2024-07-26 03:04:23 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0033|2024-07-26 03:04:23 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0034|2024-07-26 03:04:23 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0035|2024-07-26 03:04:23 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0036|2024-07-26 03:04:23 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0037|2024-07-26 03:04:23 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0038|2024-07-26 04:03:42 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0039|2024-07-26 04:03:42 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0040|2024-07-26 04:03:42 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0041|2024-07-26 04:03:42 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0042|2024-07-26 04:03:42 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0043|2024-07-26 04:03:42 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0044|2024-07-26 04:03:42 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0045|2024-07-26 05:03:01 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0046|2024-07-26 05:03:01 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0047|2024-07-26 05:03:01 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0048|2024-07-26 05:03:01 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0049|2024-07-26 05:03:01 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0050|2024-07-26 05:03:01 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0051|2024-07-26 05:03:01 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0052|2024-07-26 06:02:20 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0053|2024-07-26 06:02:20 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0054|2024-07-26 06:02:20 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0055|2024-07-26 06:02:20 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0056|2024-07-26 06:02:20 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0057|2024-07-26 06:02:20 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0058|2024-07-26 06:02:20 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0059|2024-07-26 07:01:39 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0060|2024-07-26 07:01:39 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0061|2024-07-26 07:01:39 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0062|2024-07-26 07:01:39 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0063|2024-07-26 07:01:39 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0064|2024-07-26 07:01:39 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0065|2024-07-26 07:01:39 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0066|2024-07-26 08:00:58 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0067|2024-07-26 08:00:58 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0068|2024-07-26 08:00:58 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0069|2024-07-26 08:00:58 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0070|2024-07-26 08:00:58 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0071|2024-07-26 08:00:58 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0072|2024-07-26 08:00:58 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0073|2024-07-26 09:00:17 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0074|2024-07-26 09:00:17 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0075|2024-07-26 09:00:17 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1542', remote='link-mtu 1342'
0076|2024-07-26 09:00:17 WARNING: 'tun-mtu' is used inconsistently, local='tun-mtu 1500', remote='tun-mtu 1300'
0077|2024-07-26 09:00:17 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0078|2024-07-26 09:00:17 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0079|2024-07-26 09:00:17 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
Ensuite le log du package mais rien a part l’install :
0000|+ echo '*******************Begin of package installation******************'
0001|*******************Begin of package installation******************
0002|+ touch /tmp/jeedom_install_in_progress_openvpn
0003|+ echo 1
0004|+ echo 2
0005|+ sudo killall apt apt-get unattended-upgr
0006|apt: no process found
0007|apt-get: no process found
0008|unattended-upgr: no process found
0009|+ sudo rm /var/lib/apt/lists/lock
0010|+ sudo rm /var/cache/apt/archives/lock
0011|+ sudo rm /var/lib/dpkg/lock /var/lib/dpkg/lock-frontend
0012|+ sudo sudo dpkg --configure -a --force-confdef
0013|+ sudo apt update
0014|WARNING: apt does not have a stable CLI interface. Use with caution in scripts.
0015|Hit:1 http://security.debian.org/debian-security bullseye-security InRelease
0016|Hit:2 http://deb.debian.org/debian bullseye InRelease
0017|Hit:3 http://deb.debian.org/debian bullseye-updates InRelease
0018|Get:4 http://packages.openmediavault.org/public fedaykin InRelease [6187 B]
0019|Get:5 https://download.docker.com/linux/debian bullseye InRelease [43.3 kB]
0020|Ign:6 https://repo.mongodb.org/apt/ubuntu focal/mongodb-org/4.4 InRelease
0021|Hit:7 https://downloads.plex.tv/repo/deb public InRelease
0022|Hit:8 https://deb.nodesource.com/node_18.x nodistro InRelease
0023|Hit:9 https://packages.sury.org/php bullseye InRelease
0024|Hit:10 http://archive.raspberrypi.org/debian bullseye InRelease
0025|Get:11 https://repo.mongodb.org/apt/ubuntu focal/mongodb-org/4.4 Release [3094 B]
0026|Get:12 https://repo.mongodb.org/apt/ubuntu focal/mongodb-org/4.4 Release.gpg [866 B]
0027|Err:4 http://packages.openmediavault.org/public fedaykin InRelease
0028|The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 7E7A6C592EF35D13
0029|Err:12 https://repo.mongodb.org/apt/ubuntu focal/mongodb-org/4.4 Release.gpg
0030|The following signatures were invalid: EXPKEYSIG 656408E390CFB1F5 MongoDB 4.4 Release Signing Key <packaging@mongodb.com>
0031|Reading package lists...
0032|W: GPG error: http://packages.openmediavault.org/public fedaykin InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 7E7A6C592EF35D13
0033|E: The repository 'http://packages.openmediavault.org/public fedaykin InRelease' is not signed.
0034|W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: https://repo.mongodb.org/apt/ubuntu focal/mongodb-org/4.4 Release: The following signatures were invalid: EXPKEYSIG 656408E390CFB1F5 MongoDB 4.4 Release Signing Key <packaging@mongodb.com>
0035|+ echo 3
0036|+ sudo apt install -o Dpkg::Options::=--force-confdef -y openvpn
0037|WARNING: apt does not have a stable CLI interface. Use with caution in scripts.
0038|Reading package lists...
0039|Building dependency tree...
0040|Reading state information...
0041|openvpn is already the newest version (2.5.1-3).
0042|0 upgraded, 0 newly installed, 0 to remove and 5 not upgraded.
0043|+ echo 4
0044|+ php /var/www/html/core/class/../php/jeecli.php plugin dependancy_end openvpn
0045|+ echo 5
0046|+ rm /tmp/jeedom_install_in_progress_openvpn
0047|+ echo '*******************End of package installation******************'
0048|*******************End of package installation******************