Hello
J’ai refait 2 VM Jeedom sous debian 11 en 4.4beta et en 4.4 alpha
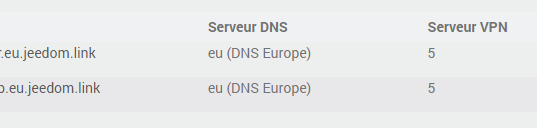
Toutes 2 avec les DNS Jeedom, sur le serveur VPN 5
L’accès n’est pas possible depuis l’extérieur j’ai
500 Internal Server Error
openresty
0000|[2023-04-02 20:06:50]DEBUG : Exec post start cmd : sudo ip link set dev mtu 1300
0001|[2023-04-02 20:14:11]DEBUG : Exec post start cmd : sudo ip link set dev mtu 1300
0000|2023-04-02 20:13:57 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
0001|2023-04-02 20:13:57 --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
0002|2023-04-02 20:13:57 WARNING: file '/tmp/jeedom/openvpn/openvpn_auth_IsbiXTLAWPKSyIu47lYaAFDk1CnJL8.conf' is group or others accessible
0003|2023-04-02 20:13:57 OpenVPN 2.5.1 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on May 14 2021
0004|2023-04-02 20:13:57 library versions: OpenSSL 1.1.1n 15 Mar 2022, LZO 2.10
0005|2023-04-02 20:13:57 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
0006|2023-04-02 20:13:57 WARNING: normally if you use --mssfix and/or --fragment, you should also set --tun-mtu 1500 (currently it is 1300)
0007|2023-04-02 20:13:57 TCP/UDP: Preserving recently used remote address: [AF_INET]135.125.10.213:1198
0008|2023-04-02 20:13:57 UDP link local: (not bound)
0009|2023-04-02 20:13:57 UDP link remote: [AF_INET]135.125.10.213:1198
0010|2023-04-02 20:13:57 VERIFY OK: depth=1, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=jeedom.com CA, name=jeedom, emailAddress=postmaster@jeedom.com
0011|2023-04-02 20:13:57 VERIFY OK: depth=0, C=FR, ST=IDF, L=Paris, O=jeedom.com, OU=jeedom.com, CN=server, name=jeedom, emailAddress=postmaster@jeedom.com
0012|2023-04-02 20:13:57 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 1024 bit RSA
0013|2023-04-02 20:13:57 [server] Peer Connection Initiated with [AF_INET]135.125.10.213:1198
0014|2023-04-02 20:14:01 Data Channel: using negotiated cipher 'AES-256-GCM'
0015|2023-04-02 20:14:01 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0016|2023-04-02 20:14:01 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
0017|2023-04-02 20:14:01 TUN/TAP device tun0 opened
0018|2023-04-02 20:14:01 net_iface_mtu_set: mtu 1300 for tun0
0019|2023-04-02 20:14:01 net_iface_up: set tun0 up
0020|2023-04-02 20:14:01 net_addr_ptp_v4_add: 10.13.49.198 peer 10.13.49.197 dev tun0
0021|2023-04-02 20:14:01 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
0022|2023-04-02 20:14:01 Initialization Sequence Completed
Je ne vois pas trop ce qui coince du coup